Looking for ways to disable or block PowerShell tools to run via cmd?
Looking for ways to prevent PowerShell attack?
In this article, we will discuss how to disable PowerShell with Group Policy (GPO) using Software Restriction Polices.
By default on Windows 10 PowerShell is enabled for all users. Hackers, attackers can utilize this to run malicious commands, access your file system, registry and more. Even ransomware can distributed throughout the network using PowerShell. Thus, for Security concern you need to disable PowerShell for all users except Administrators.
You might like - Most Important Group Policy Settings for Preventing Security Breaches
Disable PowerShell with Group Policy
#1. Finding the PowerShell.exe (executable) path.
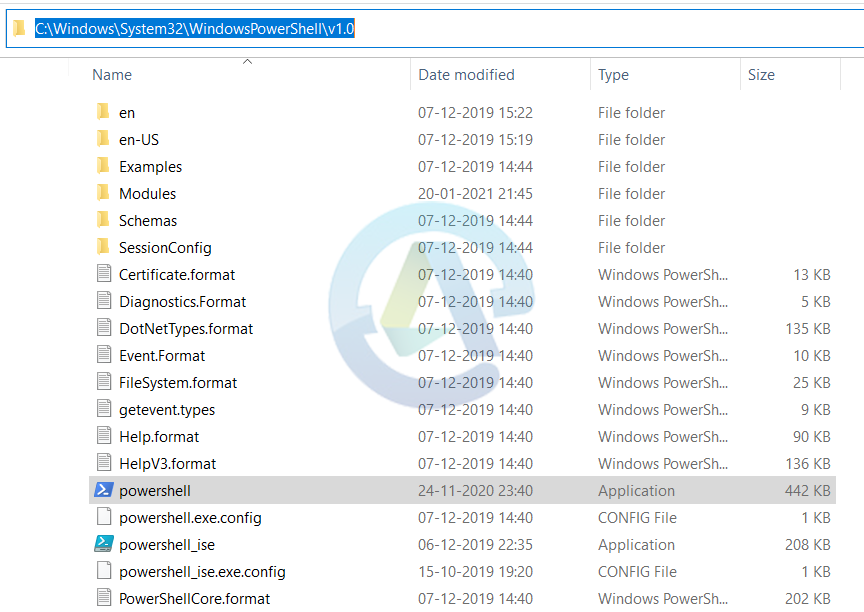
By Default location -> C:\Windows\System32\WindowsPowerShell\v1.0
You can verify this by using Task Manager. You need to launch PowerShell -> Then go to Task Manager -> in Details tab -> find powershell.exe -> Right Click on it and select “Open File Location”.
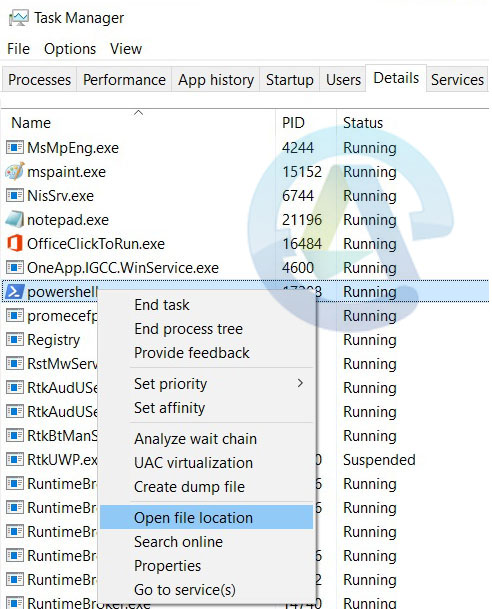
Windows explorer will take you to the folder location of powershell.exe. Check the below image for that.
#2. Create Group Policy to disable PowerShell.exe
Open the Group Policy Management Console
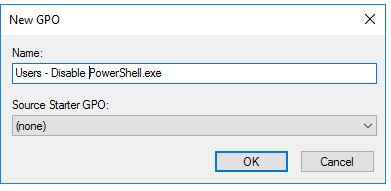
Now you have to create a new Group Policy to the OU that has the user accounts you want to block access for.
Now give the new GPO a name, Descriptive name would be best to remember and easily understood.
Once the Group policy created, you to edit the settings.
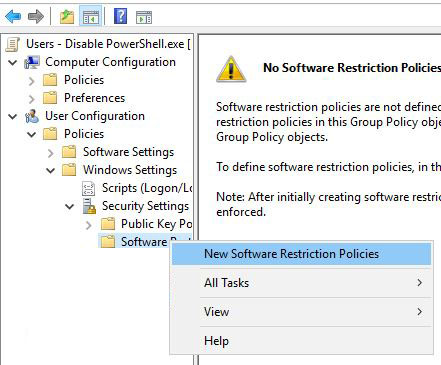
To edit the GPO, you have to navigate to -> User Configuration -> Policies -> Windows Settings -> Security Settings -> Software Restriction Policies
Now you need to right click on “Software Restriction Policies” and then select “New Software Restriction Policies”
After that you have to select the “Additional Rules”, and then right click and select “New Path Rule”
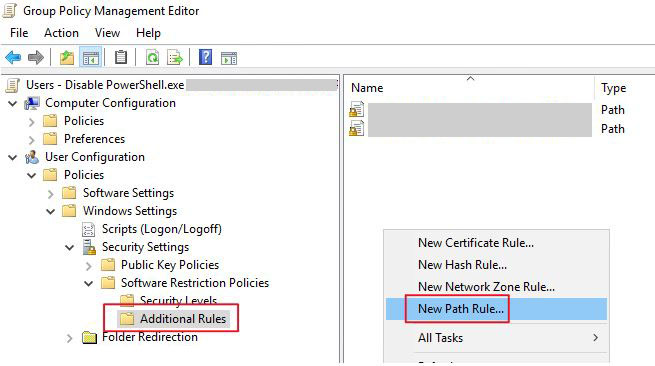
Now open the default powershell.exe path file which is -> C:\Windows\System32\WindowsPowerShell\v1.0.
Set the security level to “Disallowed” Click OK.
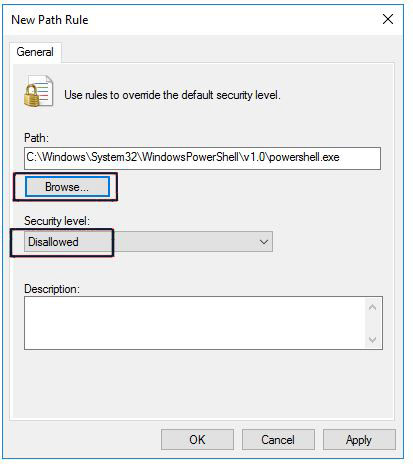
Once the above steps completed, restart the system to make GPO take effect.
Once GPO applied, whenever user try to run PowerShell receive the following error message.
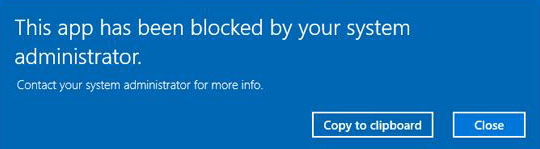
You can follow these steps for PowerShell ISE or any other software/application/tools you want to block.
Allow PowerShell for Administrators
However, you need to allow specific users like; administrator to run PowerShell and to achieve this follow the below steps.
#1. Firstly, create a new Active Directory Security group.
Give it a descriptive name which is easily understood. Something like; “GPO – Enable PowerShell”
Now you have to add users as a member to this new group whom you want to have the rights to run PowerShell.
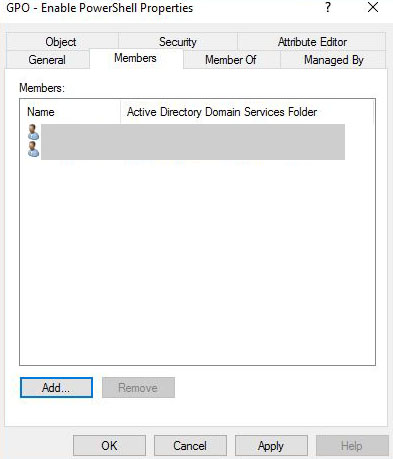
#2. Now, Modify GPO Delegation
Go to the GPO you have previously created and click on the delegation tab.
Then click on “Advanced”
After that click on “Add” and then select the security group you created that has users whom you want to enable PowerShell for. Then click OK.
Under the permissions section make sure that the group is selected and it has only these permissions.
- Read is set to “allow”
- Apply group policy is set to “Deny”
Click OK. And Reboot the computer.
Conclusion
Its always recommended to follow the Principle of Least Privilege. Only grant specific people like; Admin to have access all the resources. Users must have least privilege access.